4. Connecting to GitHub Enterprise
Prerequisites
Video Version
Introduction
EZSSH Helps you protect your code hosted in GitHub by removing the non-expiring ssh keys from the equation. Instead using your secure corporate identity to authenticate the engineers and issuing a short term SSH certificate that can be used to authenticate with GitHub.
Setting up GitHub
- Go to the EZSSH Portal https://portal.ezssh.io
- Click on Settings
- In the settings page, make sure that GitHub Certificates are enabled for your subscription.
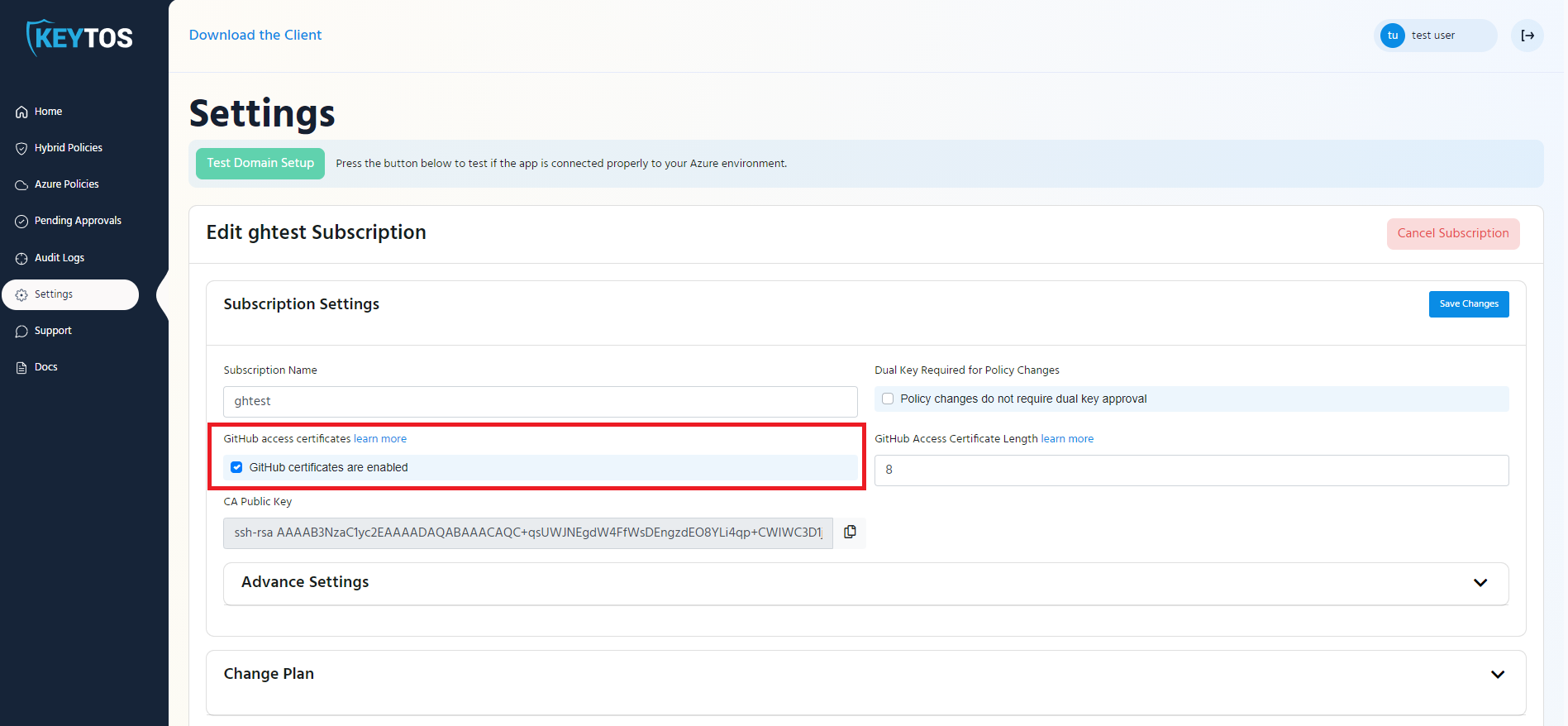
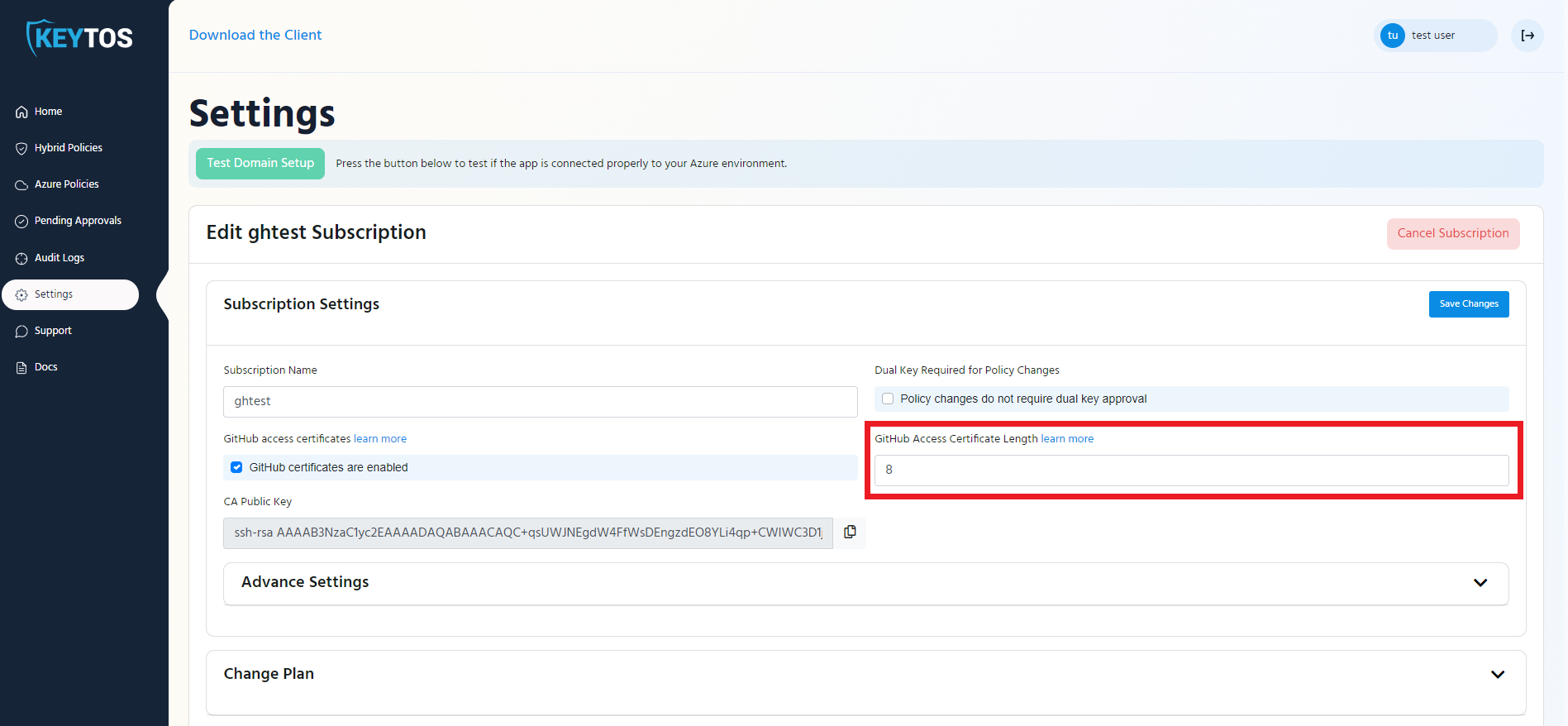
- Enter the length in hours that you want your developers certificates to last (This is how ofter the engineer has to get a new certificate). Note: In Keytos we have it set to 8 hours so our engineers only request access once a day
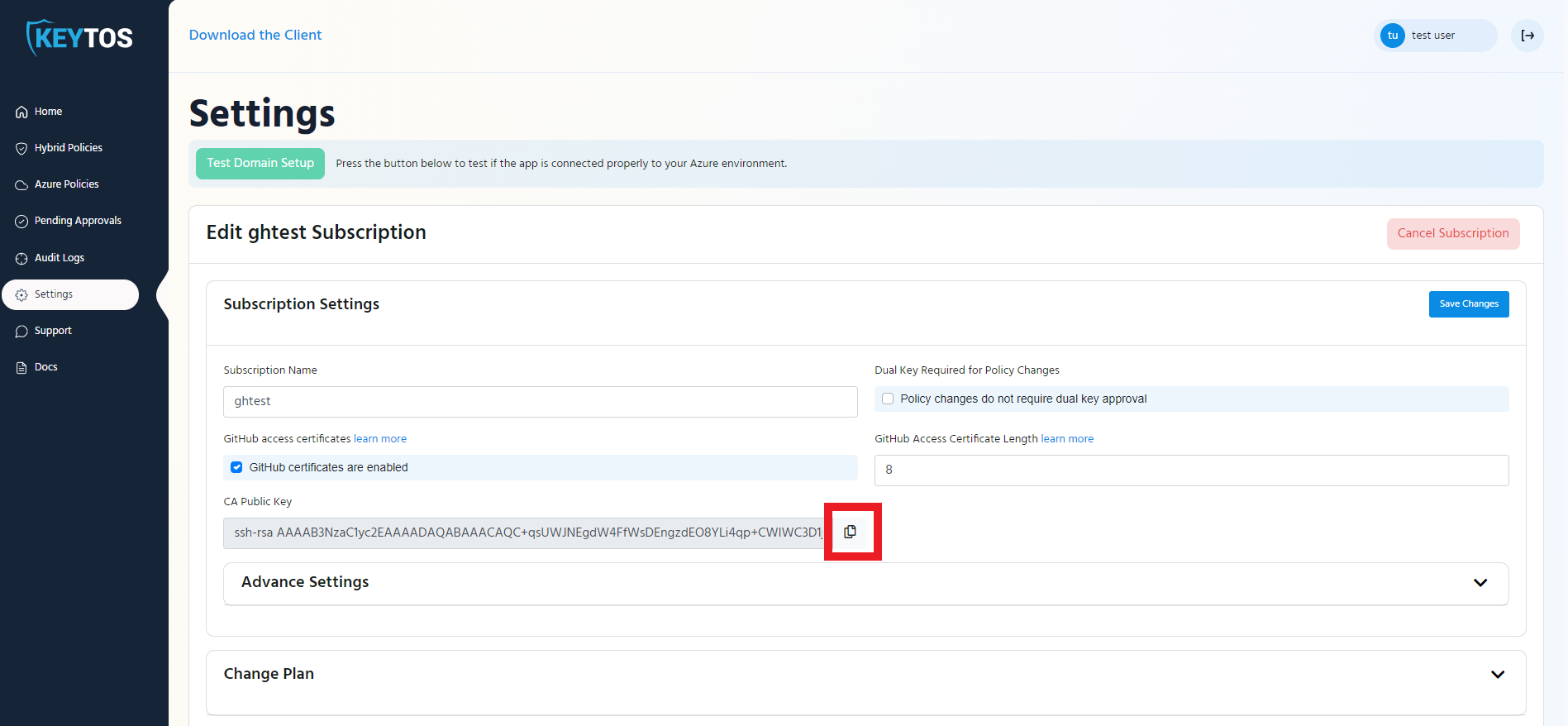
- Copy the CA Key and save it somewhere or leave this tab open. You will need it when setting up your GitHub Enterprise Security
- Go to https://github.com
- Click on your profile picture on the right
- Click on the settings button of your organization

- Click on Organization Security
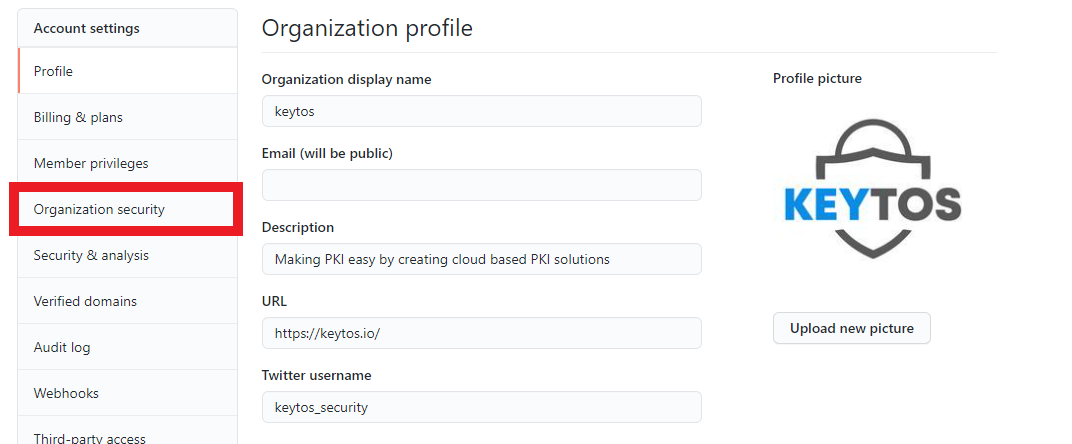
- Scroll down to “SSH Certificate Authorities, and click on the “New CA” button.
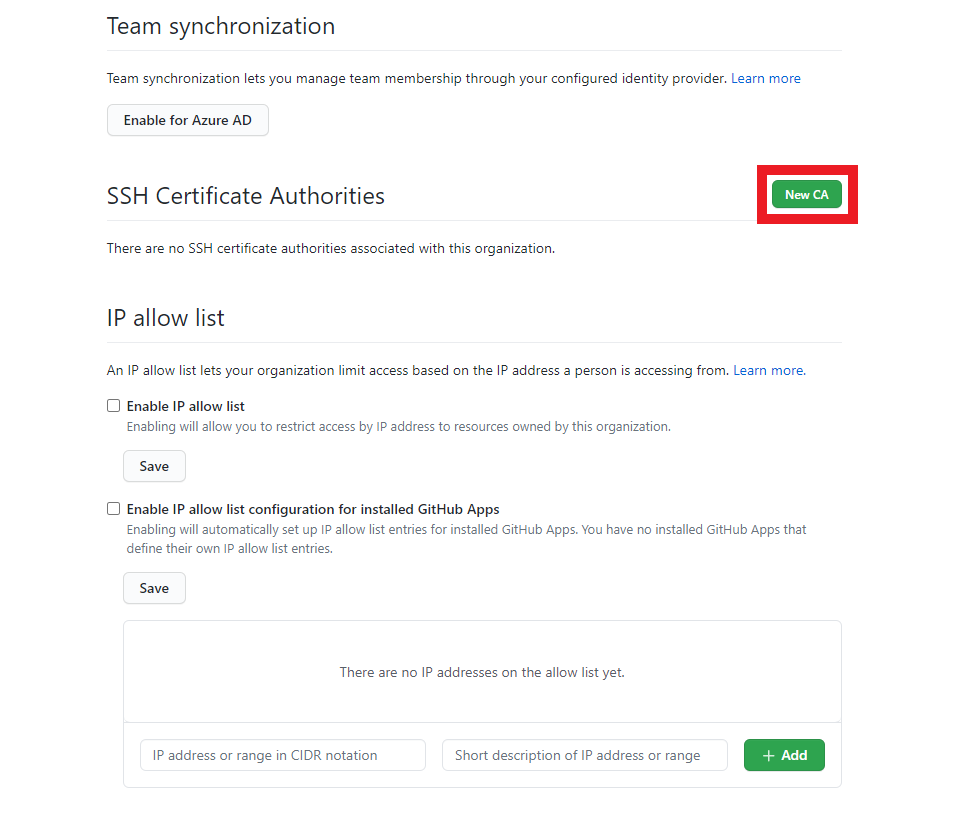
- Enter the key we copied in step 5 and click save.
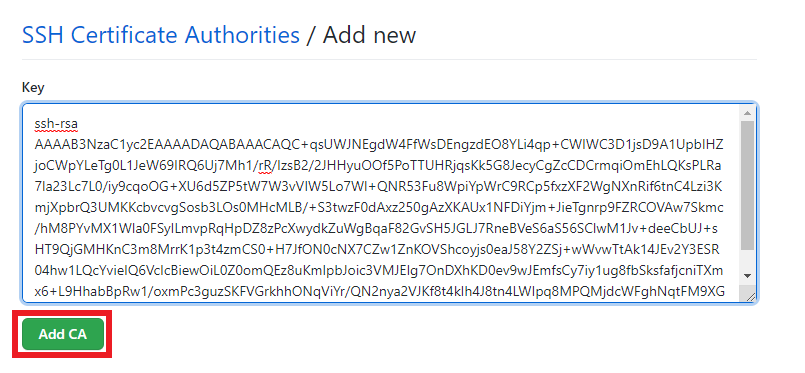
- You should now have a CA listed in your SSH Certificate Authorities.
- Click the Require SSH Certificates checkbox to only allow git operations with SSH Certificates (Recommended)
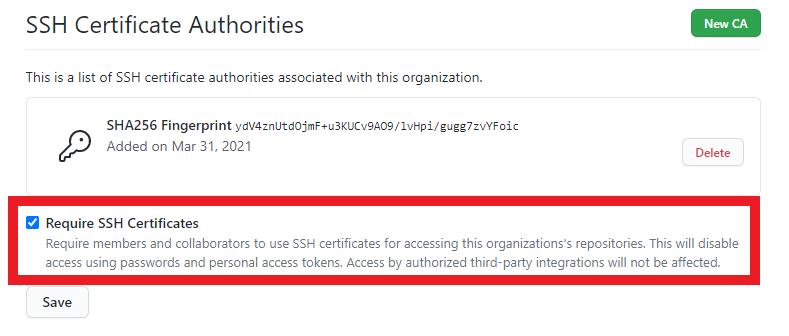
- Click the “Save” button.
EZGIT will assume that the username in the identity provider matches the user’s GitHub username. If user names are different, they will have to be mapped using the SAML mapping below.
- You are ready to start using EZSSH for GitHub
Setting Up SAML Mapping
When using GitHub Enterprise, you might let your engineers use their personal GitHub identity by linking it to your organization and their SAML Identity. To Give EZSSH Access to that mapping information, the following steps are needed:
1) Create GitHub Access Token
- First we have to create a GitHub access token. To get started, go to https://github.com and login with an account that is an owner of the organization.
- On the top right, click on your profile picture and then click on settings.
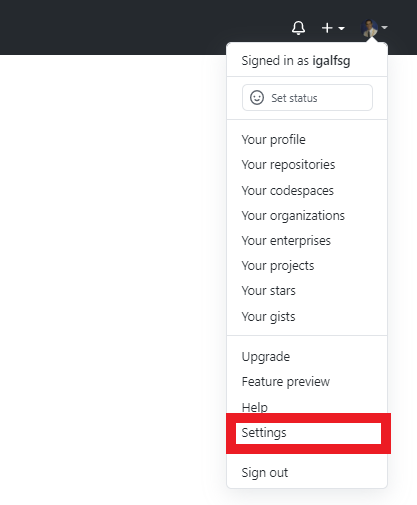
- Then Click on Developer Settings.
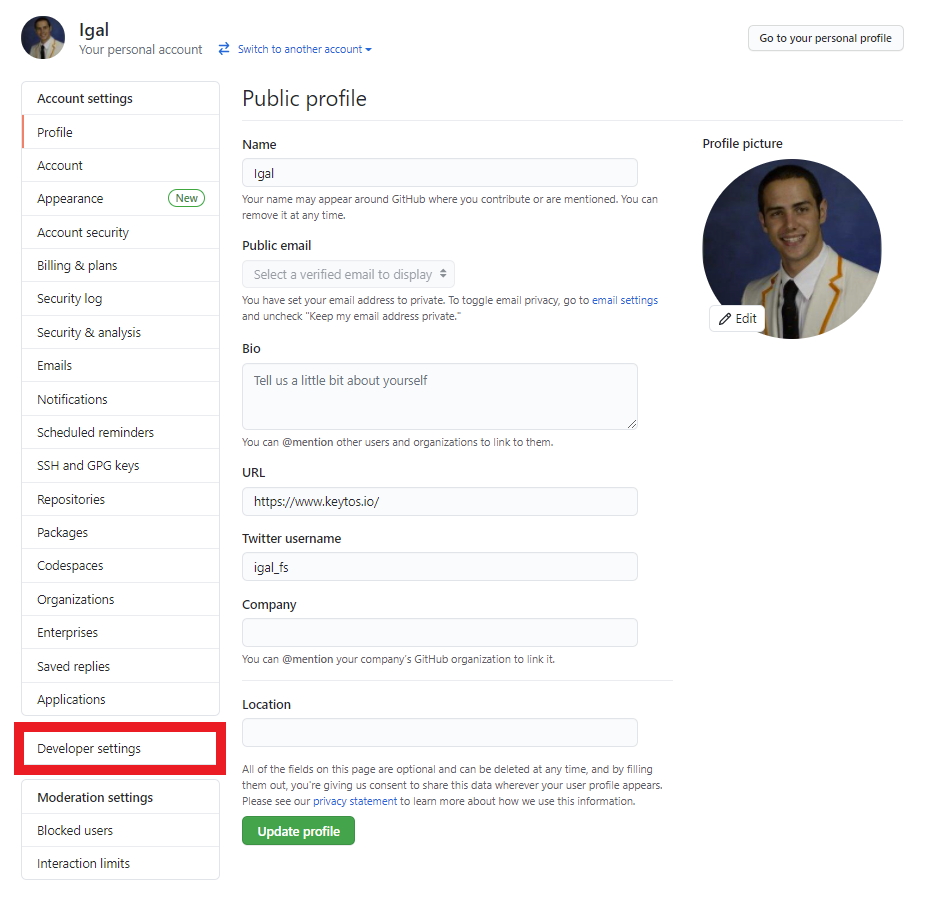
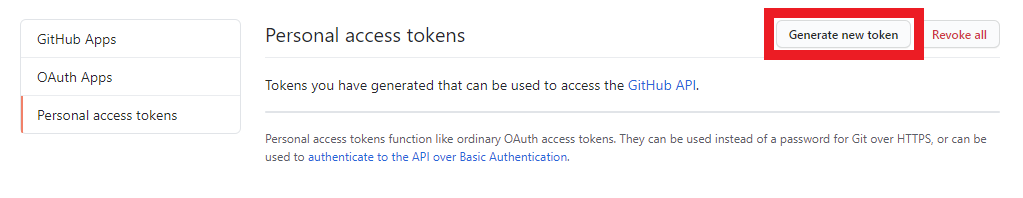
- Click on the “Personal access tokens” section.
- Click the “Generate new token” button.
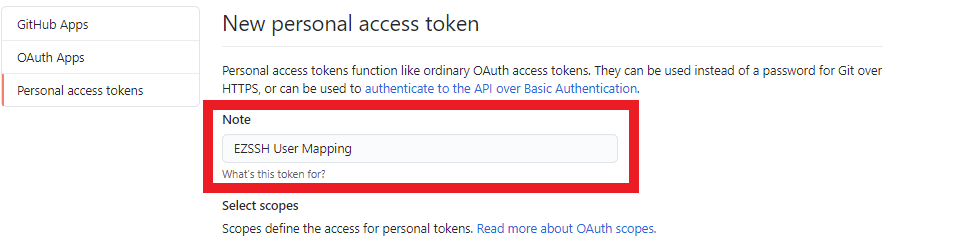
- Enter a name for the token. For Example “EZSSH User Mapping”
- Select following Scopes:
- admin:org
- read:user
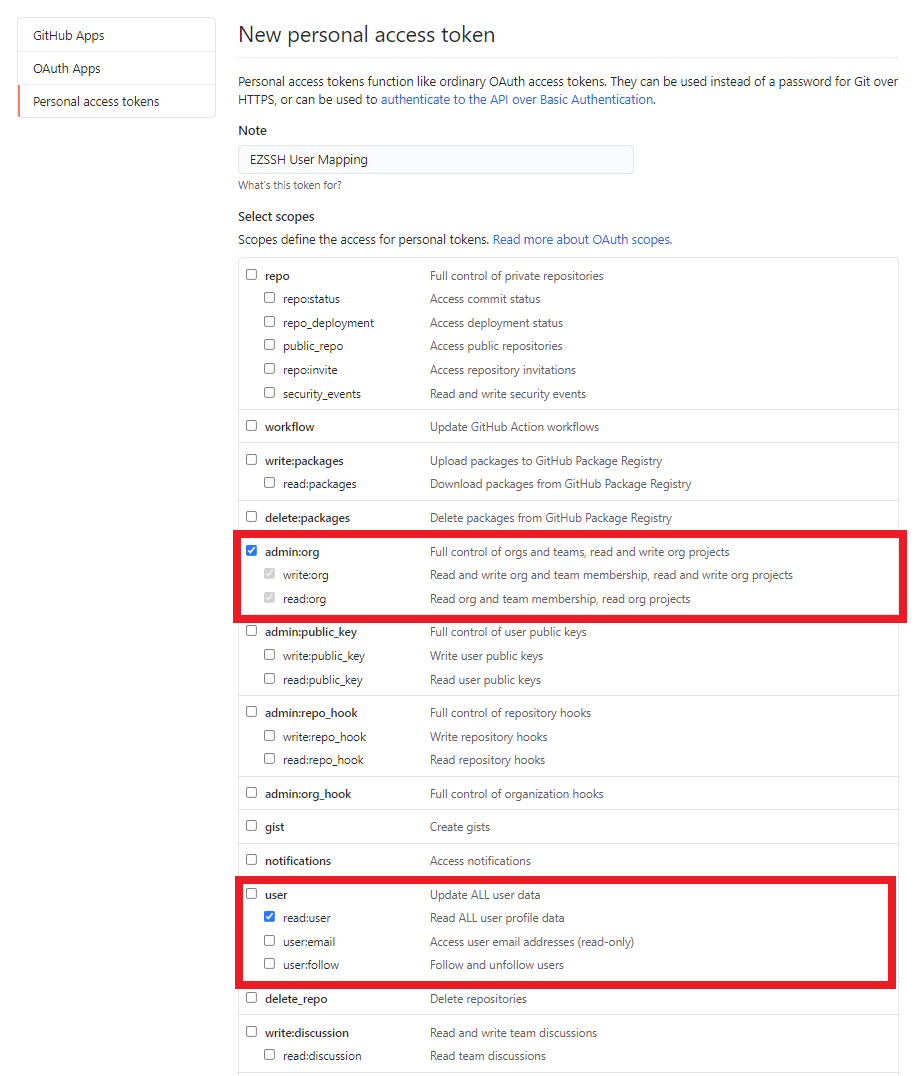
- Click the “Generate token” button.
- Copy your token (you will need it for part two).
Enabling the token for SSO
If your organization uses SSO, you will have to grant SSO Access to your token.
- Click the “Enable SSO” button.
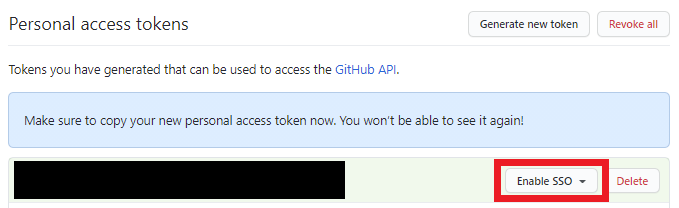
- Authenticate with your SSO Identity.
2) Add Mapping Information to EZSSH
- Once you have created your GitHub token, go to the EZSSH Portal, login with an account that owns the subscription that generates the GitHub certificates and go to settings.
- Find the correct subscription in the settings page and expand the Advance Settings Tab.
- Enable the “Map SAML Users to GitHub Users” option.
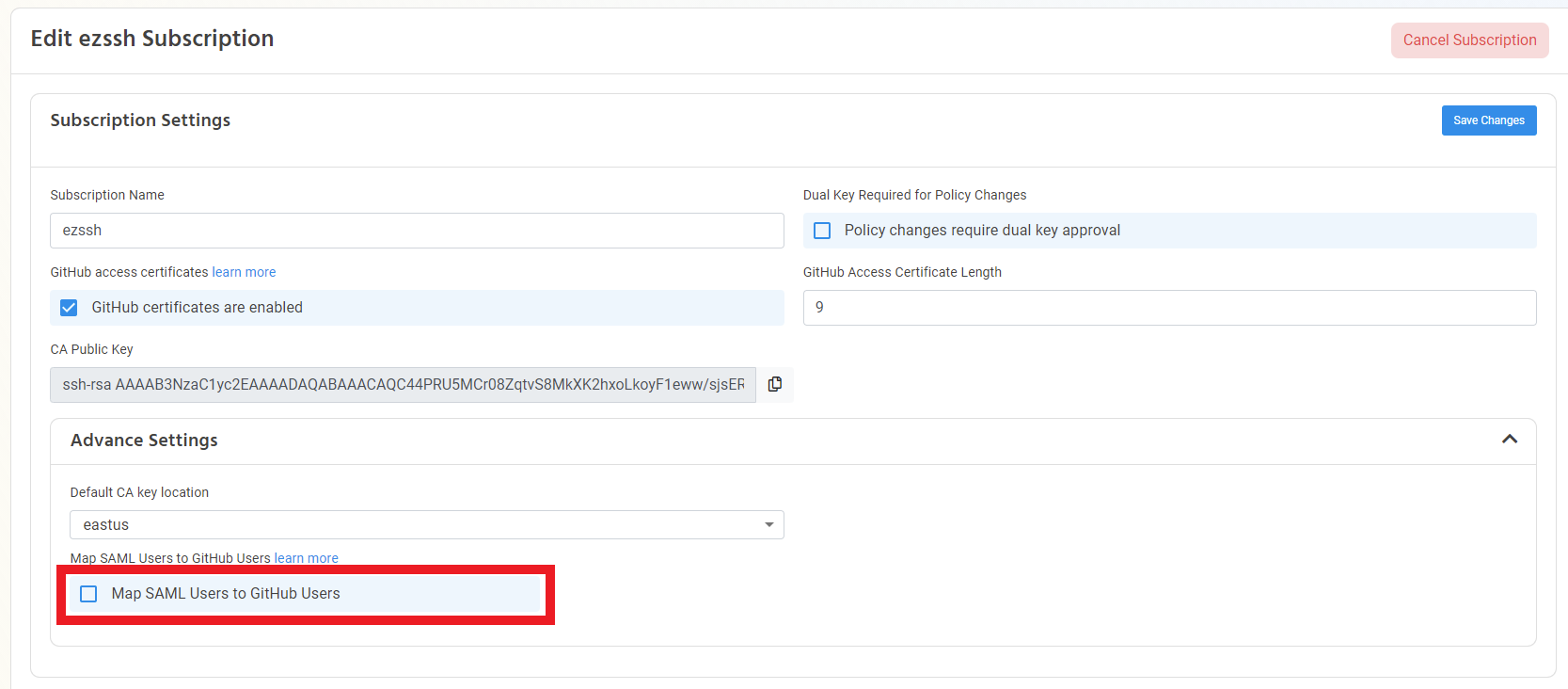
- Enter your organizations URL https://github.com/"ORGANIZATIONNAME"
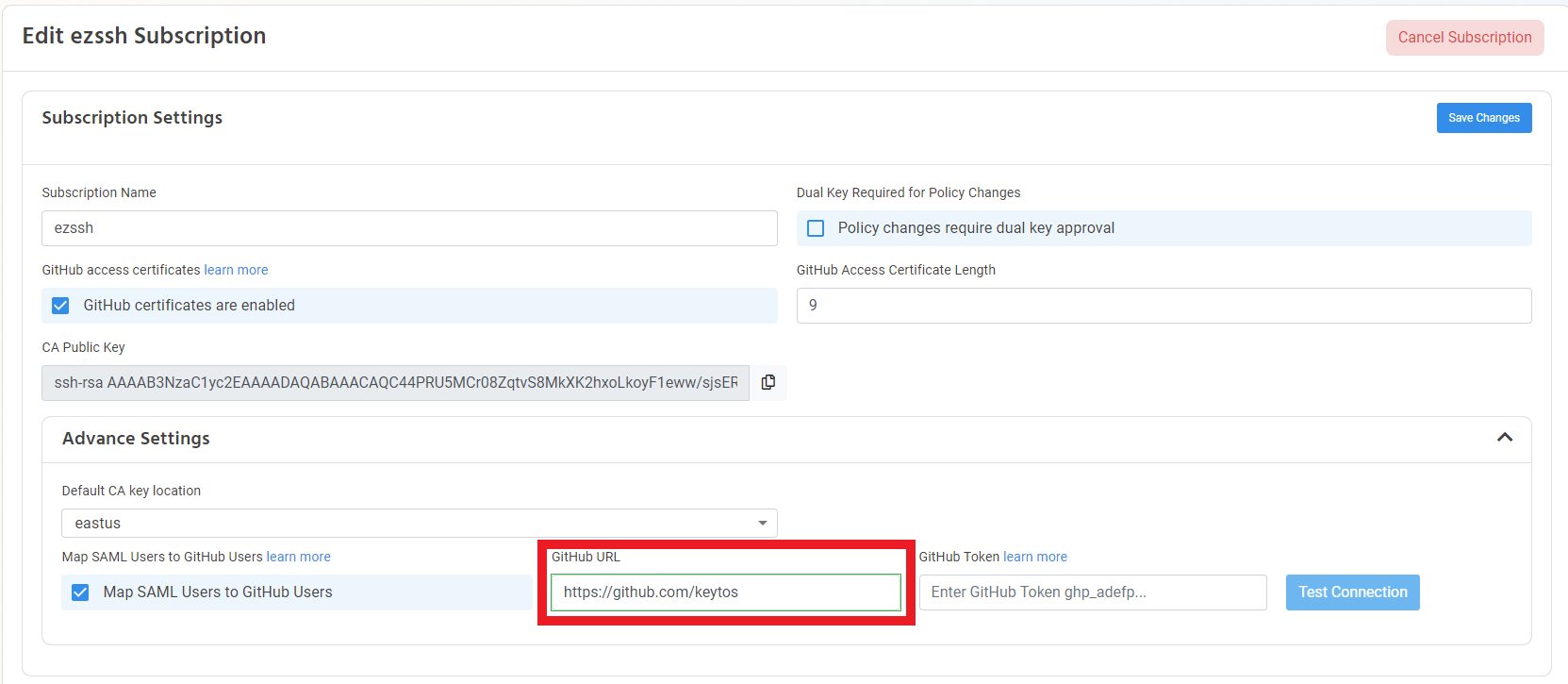
- Enter the GitHub Token generated in the previous section.
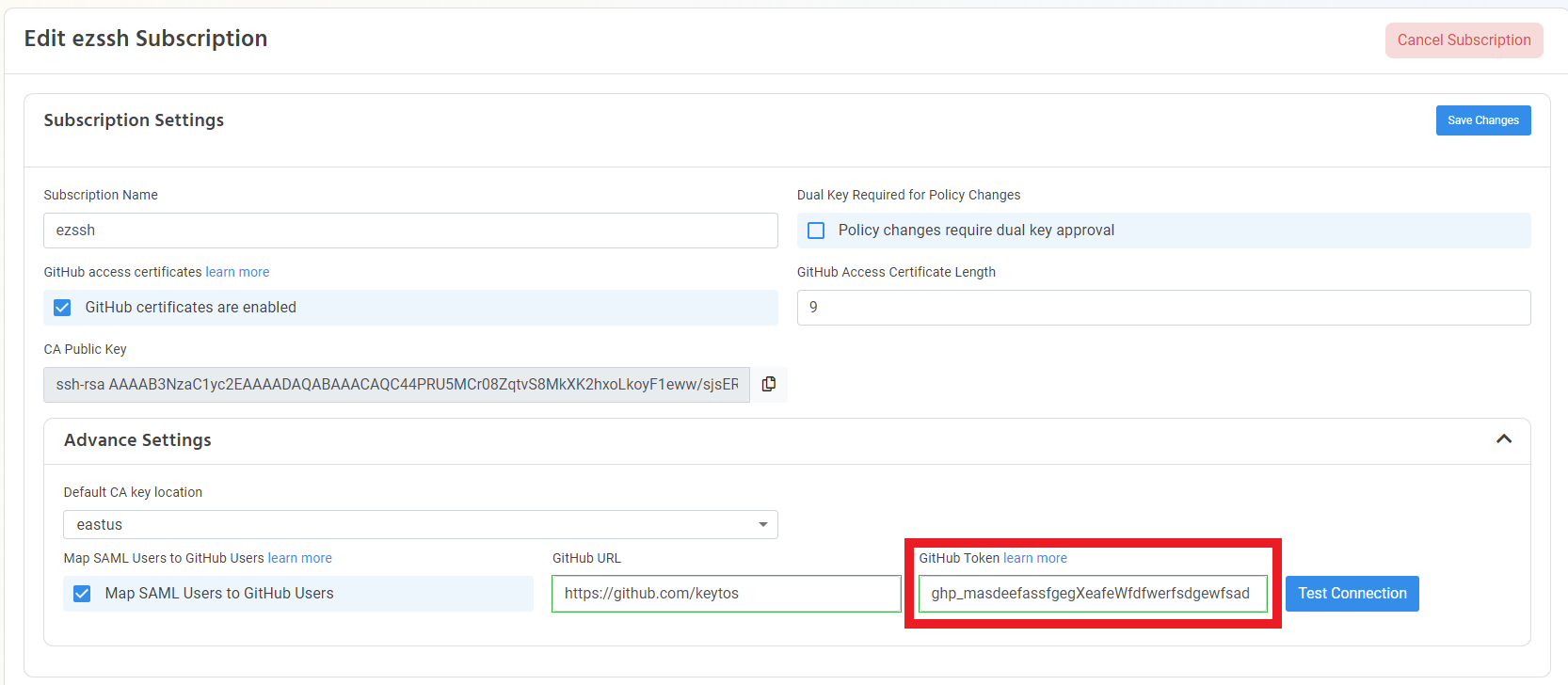
- Click Test Connection.
- If the connection is successful, click the “Save Changes” Button.
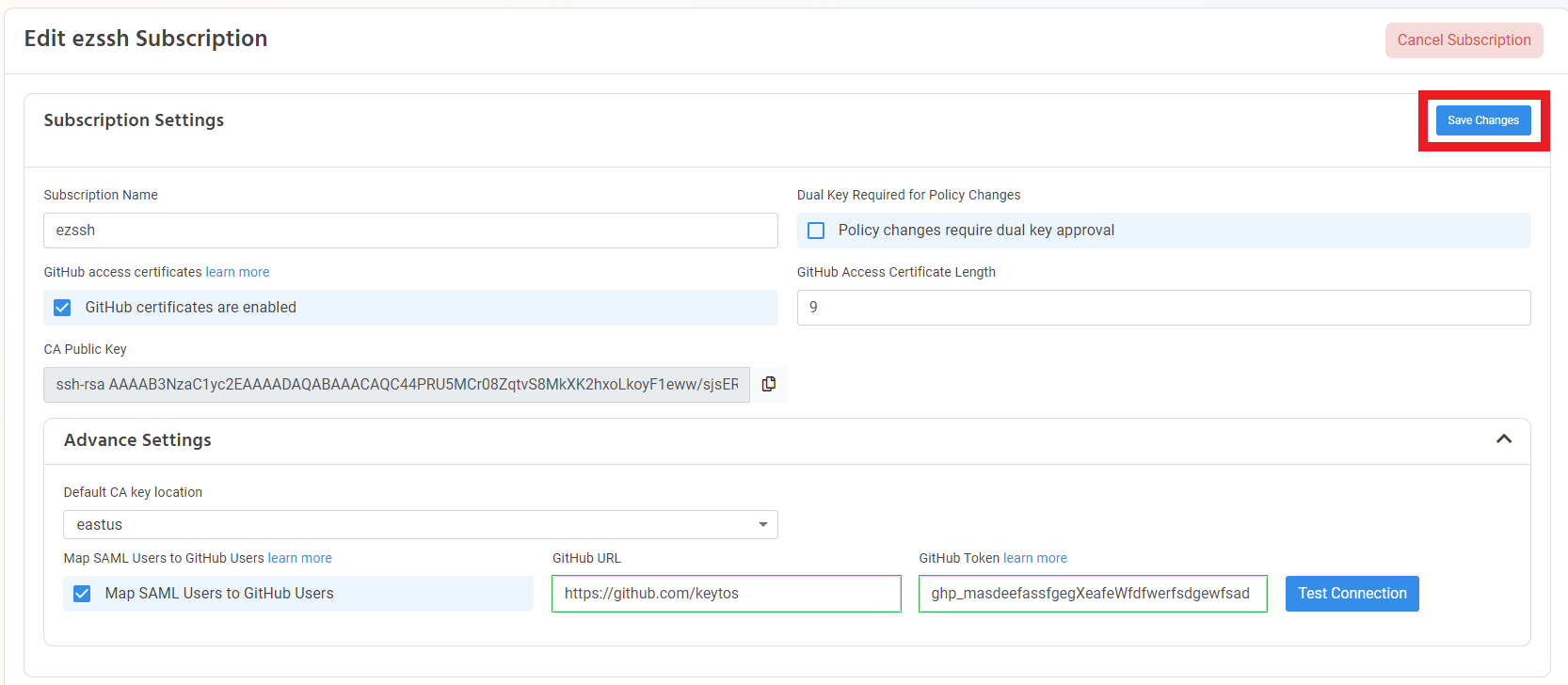
- Your users will now be mapped at least once a day.